Managed Cyber Defense Services
In today’s digital age, cyber security must be at the forefront of everything we do. Businesses need to adopt a mindset which is less reactive to threats and more proactive in nature.
Hyper connectivity demands advanced cyber security measures. Our advisory and solutions help you become hyperaware, with a system which is always learning, detecting and defending against the ever-changing threat landscape.
Vulnerability Management as a Service
A centralized platform for vulnerability monitoring and management, scanning of internal and external IP addresses for vulnerabilities, and end-to-end managed services, including reporting and remediation recommendations, in line with international best practices.
Managed Log Collection and Retention Management Service
Our Managed Log Collection and Retention Management Service is designed to meet all necessary compliance requirements for security log collection, retention and reporting.
Managed Security Information and Event Management Services
Ampersand provides Security Information and Event Management services to enable proactive monitoring of security events from clients’ source devices based on pre-defined rules. It also performs security log analysis, and reports on security risks, threats and attacks.
Managed Security Incident Management Services
Security Incident Management Services provide assistance in resolving security incidents detected by the SIEM services. This service includes coordinating with an internal security management team or a third party in order to assist in the expedition of the resolution.
Managed Endpoint Security as a Service
End point security provides a dynamic, collaborative and integrated platform to deliver protection that can outsmart attackers. The platform features multi-layered defence, static and dynamic machine learning analysis, and dynamic execution containment to stop the infections.

Cybersecurity Advisory services
Cyber Security Current State Assessment
Our security assessment services will identify each of the internal and external cyber security threats facing your information assets. We’re equipped to find vulnerabilities in vour network security as well as build a complete understanding of your IT system, i.e. from its systems to how it works. Once our assessment is complete, we’ll create a comprehensive security report with recommendations you can confidently present to management, hence ensuring that your IT spending decisions achieve maximum effect.
Develop, Implement and Maintain an Information Security Management System (ISMS)
Ampersand can offer expertise in establishing, implementing and managing an ISMS in accordance with globally recognized information security frameworks, such as ISO27001, the NIST cybersecurity framework. Our ISMS censultancy services can:
- Improve overall security posture to reduce the appetite for risk.
- Maintain compliance with regulatory requirements.
- Ensure that activities, assets and risks related to IT Security are recorded and auditable.
- Increase the level of security and awareness of best practices through continuous training.
Develop and Conduct a Risk Management Exercise
Ampersand can guide an organization through the process of a Risk Management Exercise, which will help managers and staff understand the risks their operations face.
Assist in compliance with UAE Federal & Local Information Security standards such as NESA, ADSICv2, Dubai ISR, etc.
Ampersand is able to guide an organization or relevant business units through the compliance process for a range of different regulatory regimes.
Develop and Maintain Information Security Policies, Processes, Procedures
Ampersand can assist customers in develop information security policies and procedures to ensure compliance with regulations and help remediated any such audit issues.

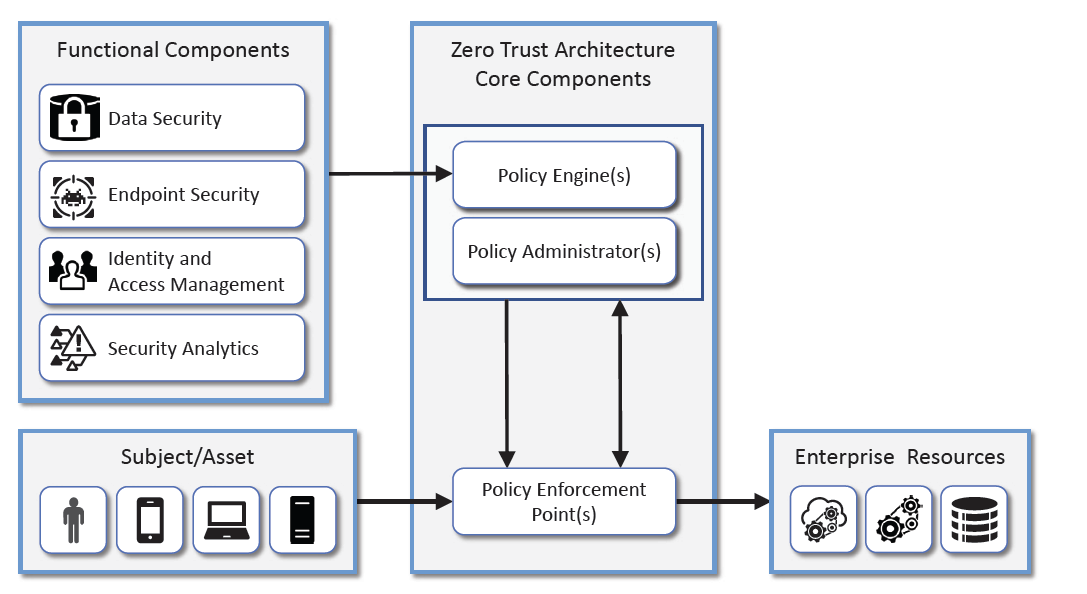
ZERO Trust
Zero trust is a cybersecurity strategy that focuses on moving perimeter-based defenses from wide, static perimeters to narrow dynamic and risk-based access control for enterprise resources regardless of where they are located. Zero trust access control is based on a number of attributes such as identity and endpoint health